C|Ct - Certified Cybersecurity Technician Course 2024
C|Ct - Certified Cybersecurity Technician Course 2024
Published 4/2024
MP4 | Video: h264, 1920x1080 | Audio: AAC, 44.1 KHz
Language: English
| Size: 6.55 GB[/center]
| Duration: 12h 22m
Build Your Cybersecurity Skills from Scratch! Master Fundamentals and Prepare for the Certification Exam.
What you'll learn
Be ready to attempt the EC-Council's Certified Cybersecurity Technician Exam (C|CT) in 2024
Recognizing information security threats, vulnerabilities, and attack vectors.
Exploring diverse categories of malware and their functionalities.
Examining principles and practices of network security.
Mastering the concepts of identification, authentication, and authorization mechanisms.
Implementing network security controls for enhanced protection.
Analyzing application security frameworks and best practices.
Understanding the intricacies of securing cloud environments.
Ensuring robust security protocols for wireless networks.
Addressing security concerns specific to mobile devices and applications.
Delving into the fundamentals of cryptography and encryption techniques.
Utilizing troubleshooting, monitoring, and analysis tools for network security.
Developing strategies for incident handling and rapid response.
Exploring the methodologies of computer forensics for digital investigations.
Requirements
No prior cybersecurity/IT knowledge needed. You will learn everything from Beginner to Master.
Eagerness to learn about cybersecurity
Description
Are you ready to embark on an exhilarating journey into the realm of cybersecurity? Look no further than our groundbreaking Certified Cybersecurity Technician course! Crafted to equip you with indispensable knowledge and skills requisite for a thriving career in cybersecurity, this course serves as your gateway to unparalleled success in the digital realm.Why Should You Enroll?EC Council Certification Prep: This course is meticulously crafted to prepare you for the prestigious EC Council Certified Cybersecurity Technician (CCT) exam, ensuring you're fully equipped with the knowledge and skills required to ace it.Expert Guidance: Learn from industry experts who have years of hands-on experience in the field of cybersecurity. Gain insights, tips, and tricks directly from seasoned professionals, giving you a competitive edge in the cybersecurity landscape.Comprehensive Curriculum: Dive deep into essential cybersecurity concepts, including network security, cryptography, ethical hacking, incident response, and more. Our comprehensive curriculum covers all the necessary topics outlined in the CCT exam blueprint, ensuring you're well-prepared for success.Flexible Learning: Access the course content anytime, anywhere, at your own pace. Whether you're a busy professional or a student, our flexible learning approach allows you to balance your studies with your other commitments.Additional ItemsPre-Made Notes for Every Module: We understand the importance of efficient studying. That's why we provide pre-made notes for every module, allowing you to review key concepts quickly and effectively, saving you valuable time and energy.Quiz for Each Module: Reinforce your understanding and gauge your progress with quizzes at the end of each module. Test your knowledge, identify areas for improvement, and solidify your grasp on the material through interactive assessments.Available on Web, iPhone, or Android: Access our course anytime, anywhere, from any device! Whether you prefer to study on your laptop, iPhone, or Android device, our platform ensures seamless learning across all your devices, offering unparalleled convenience and flexibility.Prompt Instructor Support: Have questions or need clarification? Our dedicated instructors are here to help! Enjoy prompt responses to your queries, ensuring you receive the guidance and support you need throughout your learning journey.Average Salaries in CybersecurityCybersecurity Engineer: $141,451Application Security Engineer: $140,792Cybersecurity Architect: $123,500Unlock Your Potential in CybersecurityDon't just dream of a career in cybersecurity—make it a reality with the Certified Cybersecurity Technician course. Enroll now and embark on your journey towards becoming a certified cybersecurity professional!
Overview
Section 1: Introduction
Lecture 1 Introduction
Lecture 2 The Blueprint
Lecture 3 Understanding the Course Outline (Important)
Lecture 4 About the Exam
Section 2: Module 1: Information Security Threats and Vulnerabilities
Lecture 5 Introduction
Lecture 6 Threat Sources
Lecture 7 Threat Actors/Agents
Lecture 8 Malware and it's types
Lecture 9 Define Vulnerabilities
Lecture 10 Different Types of Vulnerabilities
Section 3: Module 2: Information Security Attacks
Lecture 11 Introduction
Lecture 12 Information Security Attacks
Lecture 13 Hacking Methodologies and Frameworks
Lecture 14 Network-level Attacks
Lecture 15 Application-level and OS-level Attacks
Lecture 16 Social Engineering Attacks
Lecture 17 Wireless Network-specific Attacks
Lecture 18 IoT, OT, and Cloud Attacks
Lecture 19 Cryptographic Attacks
Section 4: Module 3: Network Security Attacks
Lecture 20 Introduction
Lecture 21 Information Security Fundamentals
Lecture 22 Network Security Fundamentals
Section 5: Module 4: Identification, Authentication and Authorization
Lecture 23 Introduction
Lecture 24 Access Control Principles, Terminologies, and Models
Lecture 25 Identity and Access Management (IAM)
Section 6: Module 5: Network Security Controls – Administrative Controls
Lecture 26 Introduction
Lecture 27 Regulatory Frameworks, Laws, and Acts
Lecture 28 Information Security Governance and Compliance Program
Lecture 29 Design and Develop Security Policies
Section 7: Module 6: Network Security Controls – Physical Controls
Lecture 30 Introduction
Lecture 31 Physical Security
Lecture 32 Physical Security Controls
Lecture 33 Workplace Security
Lecture 34 Environmental Controls
Section 8: Module 7: Network Security Controls – Technical Controls
Lecture 35 Introduction
Lecture 36 Network Security Protocols
Lecture 37 Network Segmentation
Lecture 38 Types of Firewalls and their Role
Lecture 39 Types of IDS/IPS and their Role
Lecture 40 Types of Honeypots
Lecture 41 Types of Proxy Servers
Lecture 42 Fundamentals of VPN
Lecture 43 Load Balancing
Section 9: Module 8: Network Security Assessment Techniques and Tools
Lecture 44 Introduction
Lecture 45 Threat Hunting
Lecture 46 Various Threat Intelligence Feeds and Sources
Lecture 47 Vulnerability Assessment
Lecture 48 Ethical Hacking Concepts
Lecture 49 Fundamentals of Penetration Testing
Lecture 50 Fundamentals of Configuration Management and Asset Management
Section 10: Module 9: Application Security
Lecture 51 Introduction
Lecture 52 Secure Application Design and Architecture
Lecture 53 Software Security Standards, Models and Frameworks
Lecture 54 Secure Application Development, Deployment and Automation
Lecture 55 Application Security Testing Techniques and Tools
Section 11: Module 10: Virtualization and Cloud Computing
Lecture 56 Introduction
Lecture 57 Virtualization Essential
Lecture 58 OS Virtualization Security and Concerns
Lecture 59 OS Virtualization Security Best Practices
Lecture 60 Understand Cloud Computing Fundamentals
Lecture 61 Insights of Cloud Security and Best Practices
Section 12: Module 11: Wireless Network Security
Lecture 62 Introduction
Lecture 63 Wireless Network Fundamentals
Lecture 64 Wireless Network Encryption Mechanism
Lecture 65 Wireless Network Authentication Methods
Lecture 66 Wireless Network Security Measures
Section 13: Module 12: Mobile Device Security
Lecture 67 Introduction
Lecture 68 Various Mobile Device Connection Methods
Lecture 69 Mobile Device Management Concepts
Lecture 70 Common Mobile Usage Policies in Enterprise
Lecture 71 Security Risks and Guidelines Associated with Enterprise Mobile Usage Policies
Lecture 72 Implement Enterprise-Level Mobile Security Management Solutions
Lecture 73 Implement General Security Guidelines and Best Practices on Mobile Platforms
Section 14: Module 13: IoT and OT Security
Lecture 74 Introduction
Lecture 75 IoT Devices, Application Areas, and Communication Models
Lecture 76 Security in IoT enabled Environments
Lecture 77 OT Concepts, Devices, and Protocols
Lecture 78 Security in OT-enabled Environments
Section 15: Module 14: Cryptography
Lecture 79 Introduction
Lecture 80 Cryptographic Security Techniques
Lecture 81 Various Cryptographic Algorithms
Lecture 82 Various Hash Functions and Cryptographic Tools
Lecture 83 PKI and Certificate Management
Lecture 84 Other Applications of Security
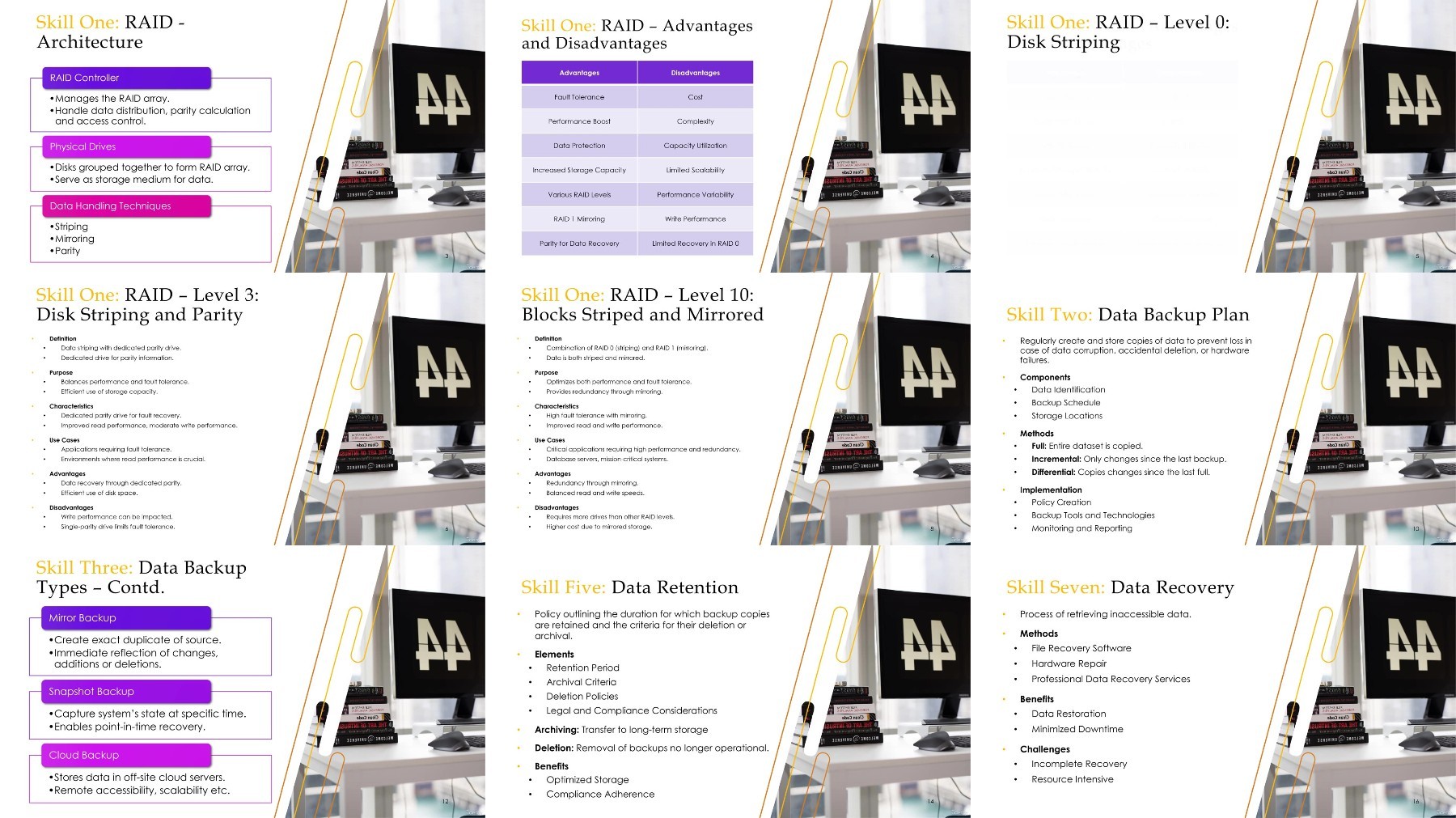
Section 16: Module 15: Data Security
Lecture 85 Introduction
Lecture 86 Data Security and its Importance
Lecture 87 Various Data Security Controls
Lecture 88 Data Backup, Retention, and Destruction
Lecture 89 Data Loss Prevention Concepts
Section 17: Module 16: Network Troubleshooting
Lecture 90 Introduction
Lecture 91 Discuss Network Troubleshooting
Lecture 92 Troubleshoot Basic Network Issues Using Utilities
Section 18: Module 17: Network Traffic Monitoring
Lecture 93 Introduction
Lecture 94 Need and Advantages of Network Traffic Monitoring
Lecture 95 Determine Baseline Traffic Signatures for Normal and Suspicious Network Traffic
Section 19: Module 18: Network Logs Monitoring and Analysis
Lecture 96 Introduction
Lecture 97 Logging Concepts
Lecture 98 Log Monitoring and Analysis on Windows
Lecture 99 Log Monitoring and Analysis on Linux
Lecture 100 Various Log Management Tools
Section 20: Module 19: Incident Response
Lecture 101 Introduction
Lecture 102 Incident response Concepts
Lecture 103 Role of First Responder in IR
Lecture 104 Incident Handling and Response Process
Section 21: Module 20: Computer Forensics
Lecture 105 Introduction
Lecture 106 Fundamentals of Computer Forensics
Lecture 107 Digital Evidence
Lecture 108 Roles and Responsibilities of Forensics Investigator
Lecture 109 Forensic Investigation Process and its Importance
Lecture 110 Various Forensic Investigation Phases
Lecture 111 Digital Evidence Sources to Support Forensic Investigation
Lecture 112 Collecting the Evidence
Lecture 113 Securing the Evidence
Lecture 114 Data Acquisition
Lecture 115 Performing Evidence Analysis
Section 22: Module 21: Business Continuity and Disaster Recovery
Lecture 116 Introduction
Lecture 117 Business Continuity and Disaster Recovery Concepts
Lecture 118 BC/DR Activities
Lecture 119 BC and DR Plan
Section 23: Module 22: Risk Management
Lecture 120 Introduction
Lecture 121 Risk Management Concepts
Lecture 122 Various Risk Management Phases
Lecture 123 Various Risk Management Frameworks
Section 24: Revision
Lecture 124 Summary - Module 1: Information Security Threats and Vulnerabilities
Lecture 125 Summary - Module 2: Information Security Attacks
Lecture 126 Summary - Module 3: Network Security Attacks
Lecture 127 Summary - Module 4: Identification, Authentication and Authorization
Lecture 128 Summary - Module 5: Network Security Administrative Controls
Lecture 129 Summary - Module 6: Physical Network Security Controls
Lecture 130 Summary - Module 7: Technical Network Security Controls
Lecture 131 Summary - Module 8: Network Security Assessment Techniques and Tools
Lecture 132 Summary - Module 9: Application Security
Lecture 133 Summary - Module 10: Virtualization and Cloud Computing
Lecture 134 Summary - Module 11: Wireless Network Security
Lecture 135 Summary - Module 12: Mobile Device Security
Lecture 136 Summary - Module 13: IoT and OT Security
Lecture 137 Summary - Module 14: Cryptography
Lecture 138 Summary - Module 15: Data Security
Lecture 139 Summary - Module 16: Network Troubleshooting
Lecture 140 Summary - Module 17: Network Traffic Monitoring
Lecture 141 Summary - Module 18: Network Logs Monitoring and Analysis
Lecture 142 Summary - Module 19: Incident Response
Lecture 143 Summary - Module 20: Computer Forensics
Lecture 144 Summary - Module 21: Business Continuity and Disaster Recovery
Lecture 145 Summary - Module 22: Risk Management
People who want to prepare for the C|CT exam.,People wanting to get their first job in cyber security industry.,Entry or Mid level professionals in IT who want to do their job tasks in a secure way.,Anybody who is eager to learn the basics of cyber security.,Beginner or professionals looking for an entry level job in cyber security.
https://voltupload.com/g7eaw2j9juy1/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z01
https://voltupload.com/junpymam5lor/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z02
https://voltupload.com/c9h5ludmbfx3/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z03
https://voltupload.com/6t5mrye5psll/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z04
https://voltupload.com/lsf7vhbzv6ej/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z05
https://voltupload.com/yyh2g1dnxy38/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z06
https://voltupload.com/952q0z3ygfef/CCT_-_Certified_Cybersecurity_Technician_Course_2024.zip
https://rapidgator.net/file/65e8ef0d2bd6b8be477f947477679f4a/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z01
https://rapidgator.net/file/4163a024c9ce5c7914620dc9d56a73df/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z02
https://rapidgator.net/file/37834e0639b2375886317d253759e0dc/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z03
https://rapidgator.net/file/ed31dd32ac6e8a0388c66a4e22072d87/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z04
https://rapidgator.net/file/61c8ab52b9ff7be053abfb16399f2792/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z05
https://rapidgator.net/file/3600f30a7f518834a6722c7551b9604c/CCT_-_Certified_Cybersecurity_Technician_Course_2024.z06
https://rapidgator.net/file/51ecab9462fe5f8fe1b95dfb635da772/CCT_-_Certified_Cybersecurity_Technician_Course_2024.zip
Free search engine download: CCT - Certified Cybersecurity Technician Course 2024
